NTAG® 213 is a very cost-effective way of deploying simple NFC stickers or cards. However, this series only supports ISO 14443-3 protocol and not ISO 7816-4 (APDU). For that reason, you might need to take some extra steps in order to use a PC/SC reader with these tags.
Note: NTAG — is a trademark of NXP B.V. This site is not affiliated with NXP.
Reading data from NTAG® 213, NTAG® 215 and NTAG® 216 tags using PC/SC reader
You would need to directly send T=CL raw commands to the tag. There is no standard way of doing it through PC/SC interface and it’s specific to the model of the particular card reader.
Here, we will show some examples for Identiv uTrust 3700 F / 3720 F reader. These readers offer PAPDU_TCL_PASS_THRU pseudo-command which can be used through PC/SC interface. In order to send a raw command with these readers, you need to wrap it in the following way:
# PAPDU_ISO14443_PART3_PASS_THRU (Mifare Pass Thru)
0xFF 0xEF 0x00 0x00 Lc Data
Where “Lc” is the length of the raw command you want to send, and “Data” is the actual raw command to send to the tag.
According to NTAG 213 manual, the “READ” command has the command code 0x30 and needs to be followed by one byte which designates the start page address. For NTAG 213, NDEF content starts at the page 0x04. Thus, our raw command to read the beginning of NDEF content would be:
0x30 0x04
and we need to wrap it into the pseudo-APDU:
0xFF 0xEF 0x00 0x00 0x02 0x30 0x04
This command will correctly read the first 16 bytes (4 pages) out of NTAG 213’s NDEF contents (assuming that you are using Identiv uTrust card reader).
If you want to read more, you need to increment the start page address by the value of 4:
0xFF 0xEF 0x00 0x00 0x02 0x30 0x08
0xFF 0xEF 0x00 0x00 0x02 0x30 0x0C
0xFF 0xEF 0x00 0x00 0x02 0x30 0x10
0xFF 0xEF 0x00 0x00 0x02 0x30 0x14
and so on.
Finding out what is the total length
In order to find out what is the total memory size of your tag, you should consult Capability Container:
0xFF 0xEF 0x00 0x00 0x02 0x30 0x03
The first four bytes returned will be the tag’s Capability Container and inside of this structure, the 2nd byte (counting from 0) will be the total memory size divided by 8.
Example for NTAG® 213:
e1 10 12 00 01 03 a0 0c 34 03 15 d1 01 11 55 04
Thus, total amount of memory is: 0x12 * 8 = 144 bytes.
Decoding data from the tag
The data on the tag is encoded with a TLV scheme. TLV stands for “Type-Length-Value”. There are multiple valid sequence types. Most of these types are containing some metadata, the most meaningful sequence type is “NDEF Message TLV” - 0x03. In most cases, you can safely ignore any other TLVs.
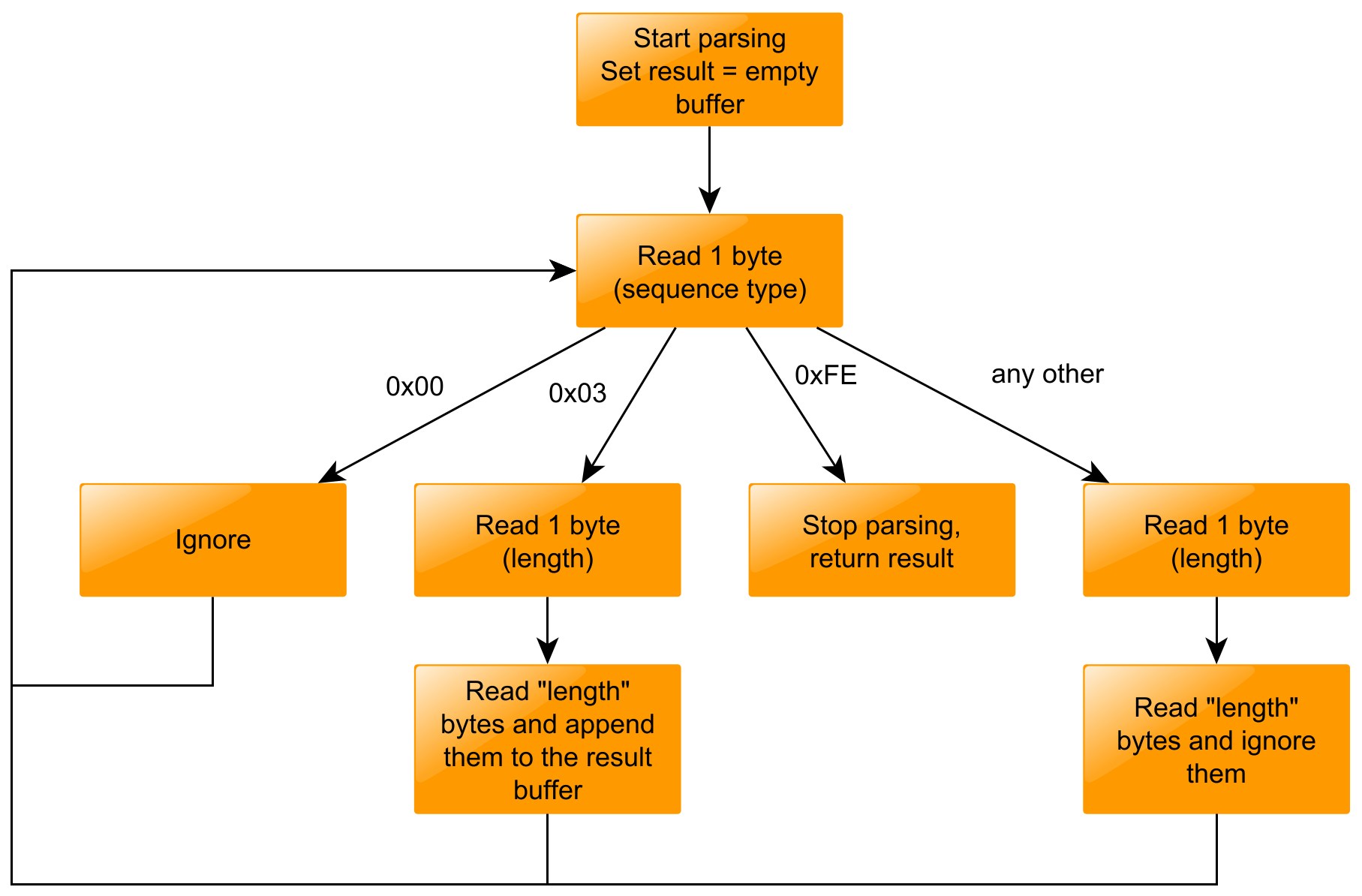
Example program in Python
The example program could be found on GitHub: icedevml/pcsc-read-ndef. Please note that program will only work with Identiv uTrust 3700F and 3720F readers. Other similiar Identiv/SCM Microsystems readers might also work fine.
