Both NXP’s NTAG® 213 (also other variants: NTAG® 215, NTAG® 216) and NTAG® 424 DNA can be programmed in such a way that they will generate a different, distinguishable URL on each tap. The main difference between NTAG® 213 series and NTAG® 424 DNA is that the latter one supports cryptography. What does that mean?
Note: This site is not affiliated with NXP. Information is provided here for descriptive purposes. NTAG — is a trademark of NXP B.V.
The simplest possible dynamic URL could be configured on NTAG 213. The dynamic part would contain only the UID and the scan counter:
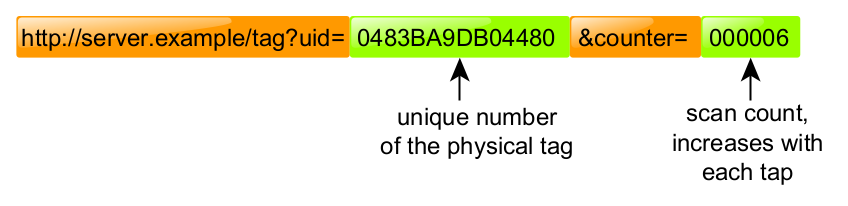
The elements marked green are the dynamic parts:
tag UID - the unique number of the physical tag assigned by the factory; it’s different for each tag; counter - the value which indicates how many times the tag was tapped to the reader;
Of course, this has one very important limitation - the user is able to edit the “uid” and the “counter” parameters in the URL. That would give him the ability to send fake information to the server without actually scanning the tag.
To account for that, NTAG 424 DNA has much more advanced capabilities for the “dynamic URL” function. In addition to the above example, there is a new parameter called “cmac”, and it contains the cryptographic signature of the dynamic data.
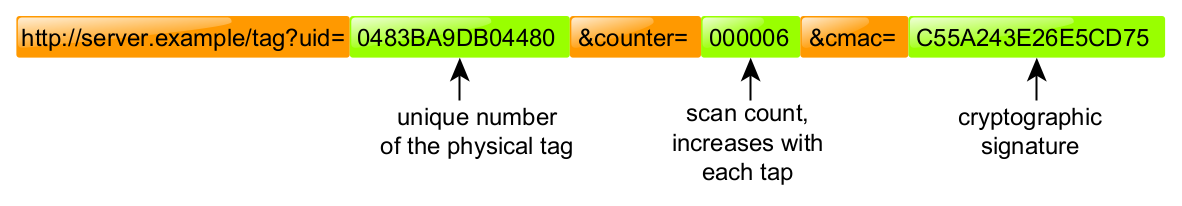
In particular, it means that each tag has its own authentication key which is securely stored in the tag’s configuration. This key is used to sign “uid” and “counter” data with a cryptographically secure signature (based on AES-CMAC algorithm). Whenever the user opens the URL, the server would validate the signature in order to check if it’s real or forged.
This process is using military-grade cryptography, so the signature mechanism is extremely hard to break. The user is not able to just edit the “uid” or “counter” parameters in the URL, because that would raise an error on the server and the access will be denied.
Technical explanation
It is safe to skip this section if you are not interested in technical details.
In the examples below, we do use COMPUTE_SIGNATURE(secret_key, tag_uid, read_counter) pseudo-function. This corresponds to the function defined in section 9.3.8.1 “AES mode MAC calculation” of NTAG 424’s datasheet. The function itself is based on AES-CMAC algorithm.
Example #1: Legitimate URL
- User opens:
http://server.example/tag?uid=0483BA9DB04480&counter=000006&cmac=C55A243E26E5CD75 - The server takes the UID and the counter parameter and computes the cryptographic signature on it’s own:
COMPUTE_SIGNATURE(key, "0483BA9DB04480", "000006") Result: "C55A243E26E5CD75" - The server takes “cmac” parameter and compares with the signature computed in step #2:
"C55A243E26E5CD75" == "C55A243E26E5CD75" - Validation is successful. The dynamic URL really came from the tag and doesn’t seem to be forged.
What would happen if the user would manually edit some parameters by hand?
Example #2: Forged URL
- User opens (please note that the part marked in red was manually edited by the user in order to forge the URL):
http://server.example/tag?uid=0483BA9DB04480&counter=000044&cmac=C55A243E26E5CD75 - The server takes the UID and the counter parameter and computes the cryptographic signature on it’s own:
COMPUTE_SIGNATURE(key, "0483BA9DB04480", "000044") Result: "FFBD3C2153A4D71D" - The server takes “cmac” parameter and compares with the signature computed in step #2:
"FFBD3C2153A4D71D" != "C55A243E26E5CD75" - Validation is FAILED, the cryptographic signature doesn’t match. The URL was forged and it doesn’t come from the real tag.
Encrypted dynamic URL
In addition to the above examples, NTAG 424 DNA also supports more advanced dynamic URL operation modes. The UID and the counter parameters may optionally be encrypted. Moreover, the encrypted dynamic URL could also carry some custom, application-specific data, for instance, the surname of the employee, product ID etc.
Summary
NTAG® 213 dynamic URL feature is great if you just want to roughly count how many people have physically interacted with your NFC tags, assuming that high reliability is not needed.
However, NTAG® 424 DNA dynamic URLs are suitable for applications that require cryptographic security. This could include user authentication, asset authentication or even some more complex schemes.
